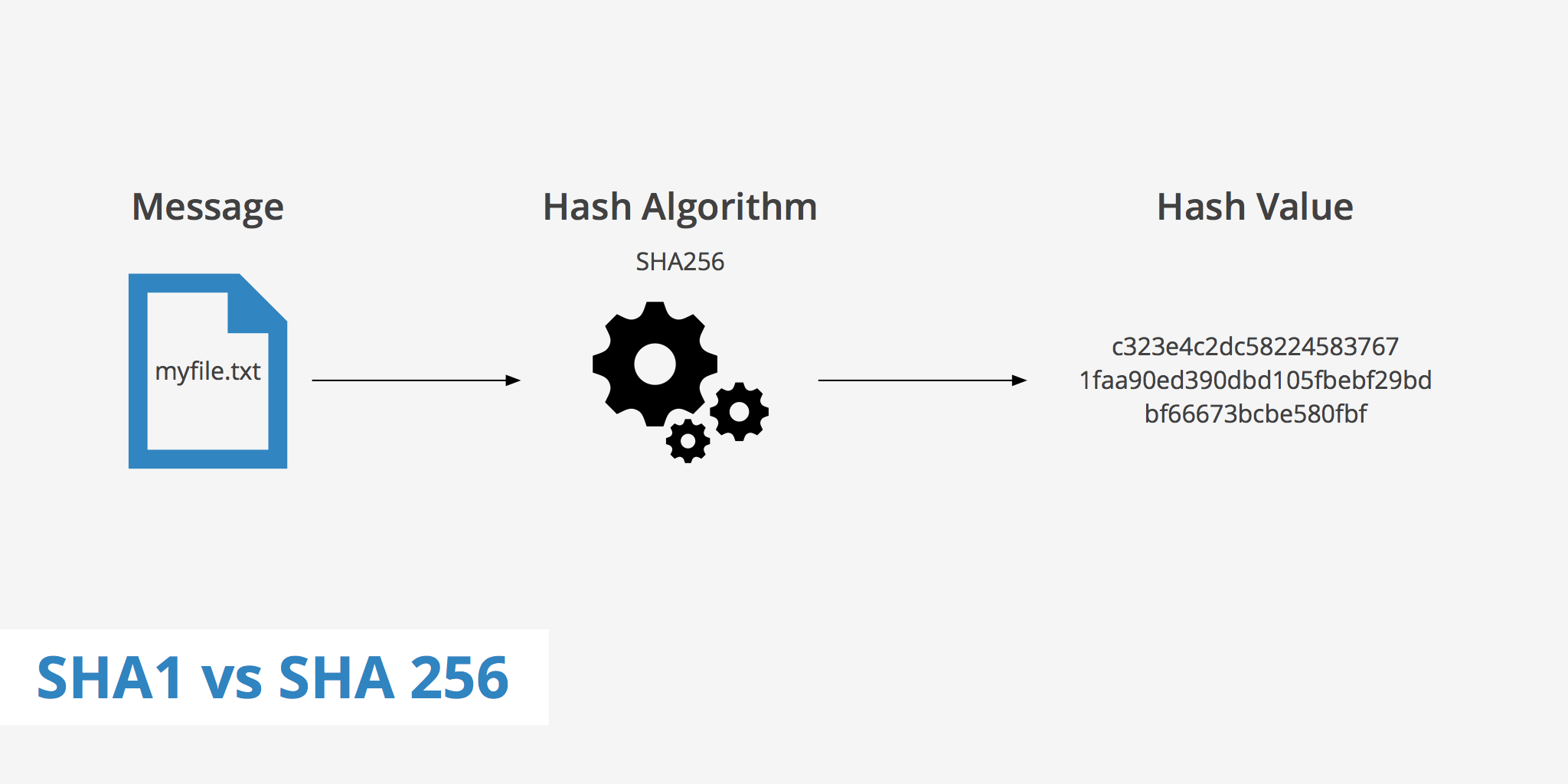
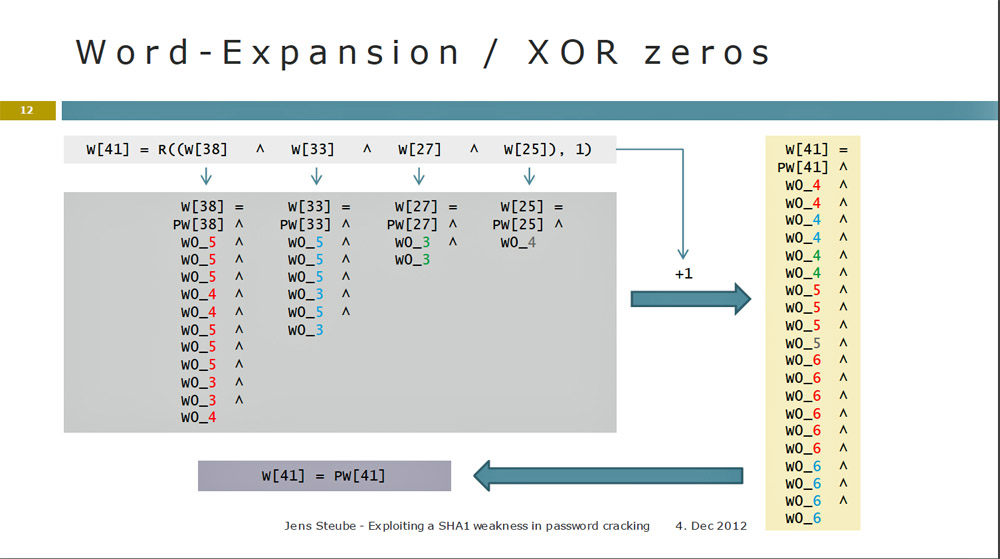
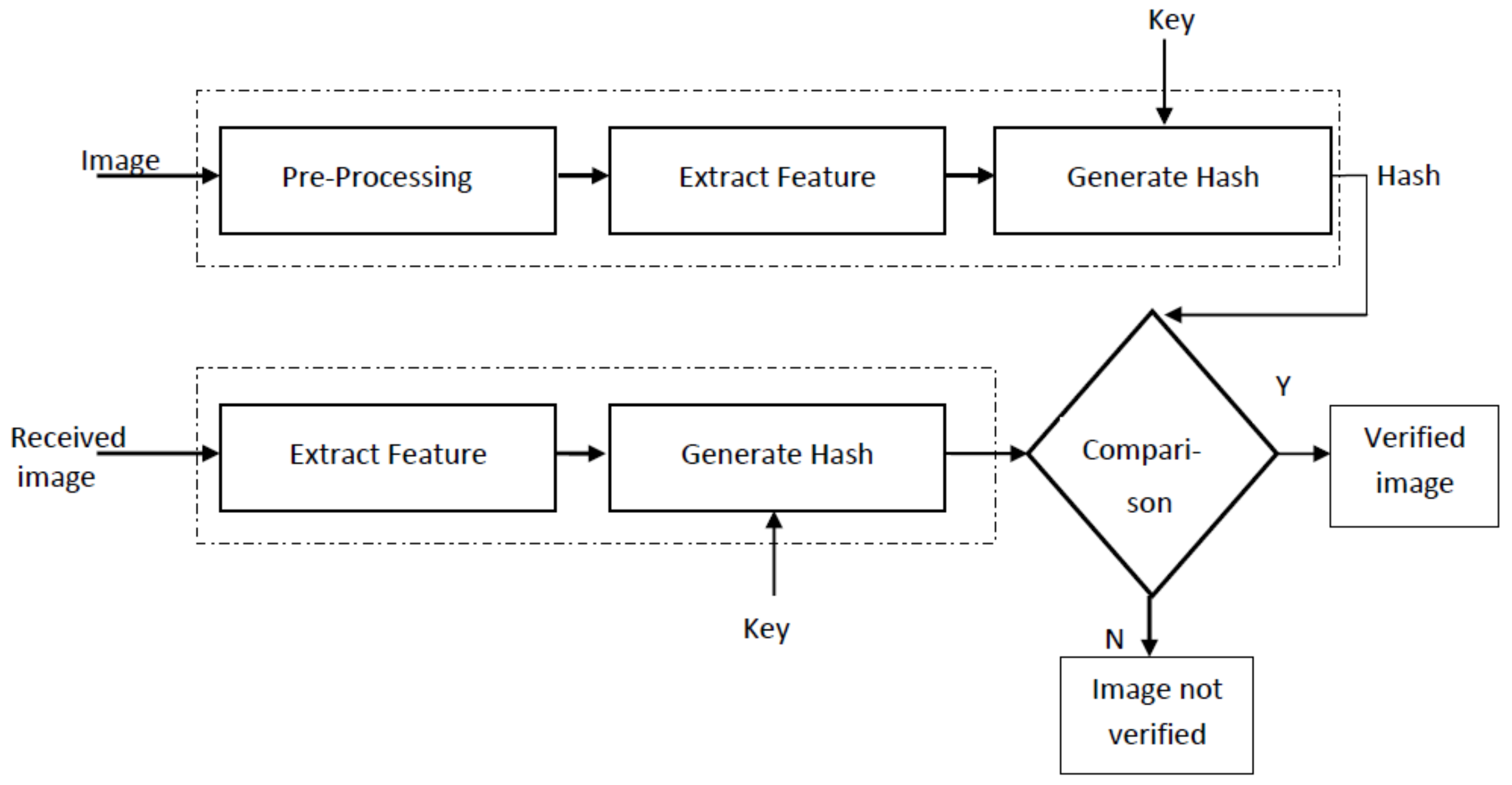
Analysis of Inappropriate Usage of Cryptographic Primitives in Indian Mobile Financial Applications | SpringerLink
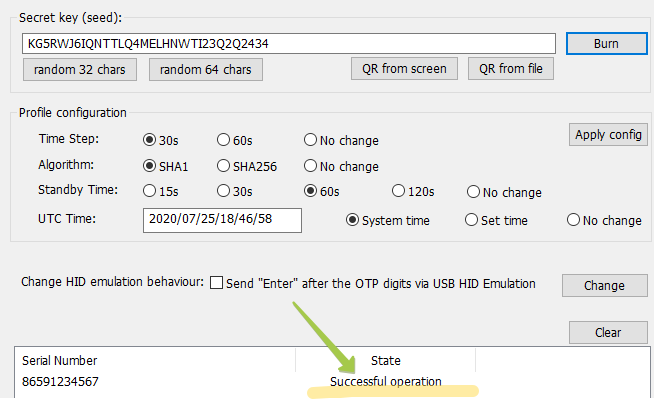
TOKEN2 Switzerland 🇨🇭 | EVVIS-QR1 USB Config tool | TOKEN2 MFA Products and Services | programmable hardware token, FIDO2 key, U2F key, TOTP, One-Time Password (OTP) Tokens | OATH-compliant Authentication Tokens and
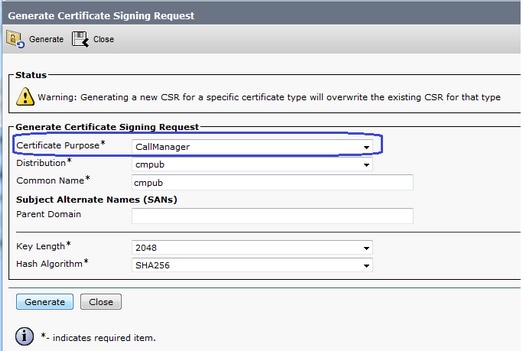
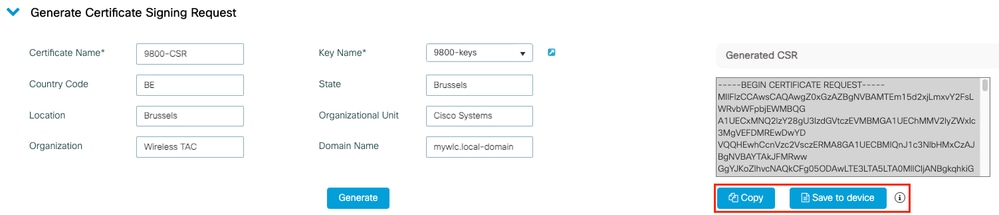
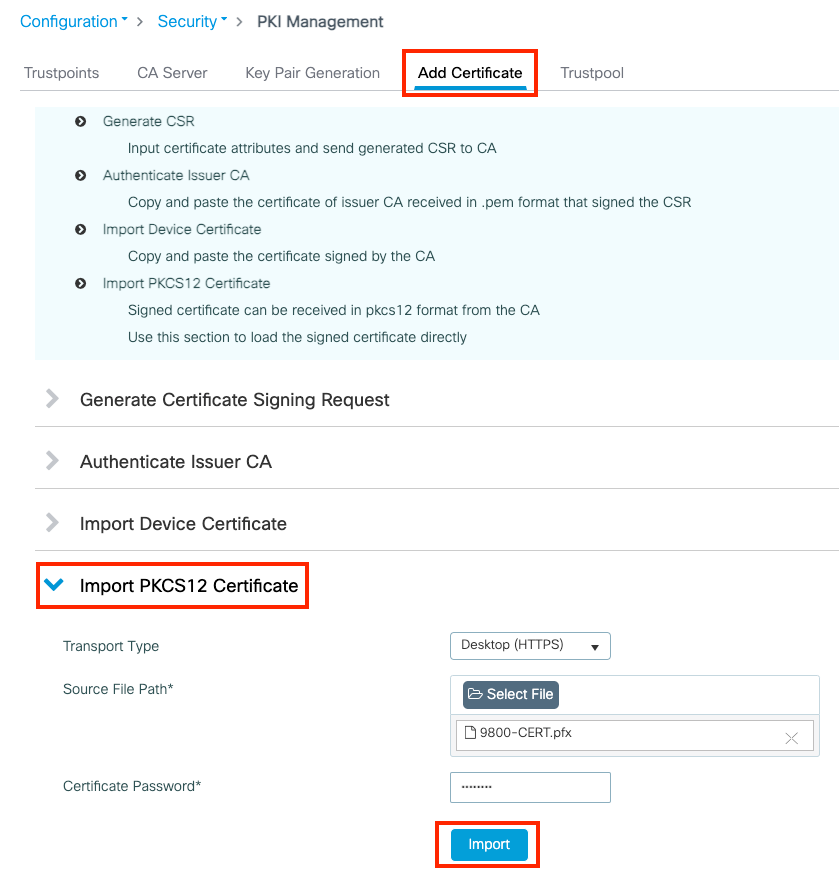
Signierte Zertifikate der Enterprise CA (Drittanbieter-CA) für SIP TLS und SRTP zwischen CUCM, IP-Telefonen und CUBE konfigurieren und Fehlerbehebung dafür durchführen - Cisco
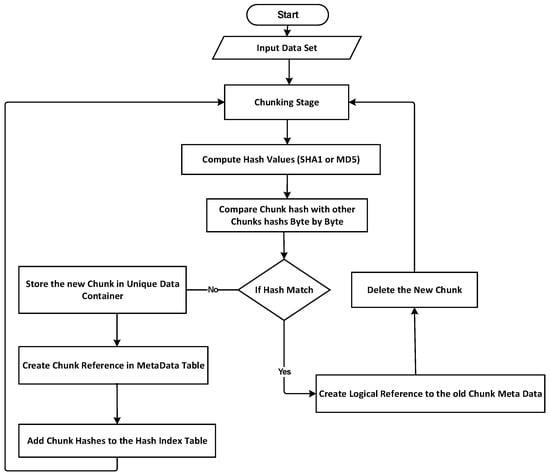
Data & Storage Services CERN IT Department CH-1211 Genève 23 Switzerland t DSS Computing for the LHC Alberto Pace - ppt download