PDF) Formal Verification of the Authentication and Voice Communication Protocol Security on Device X Using Scyther Tool
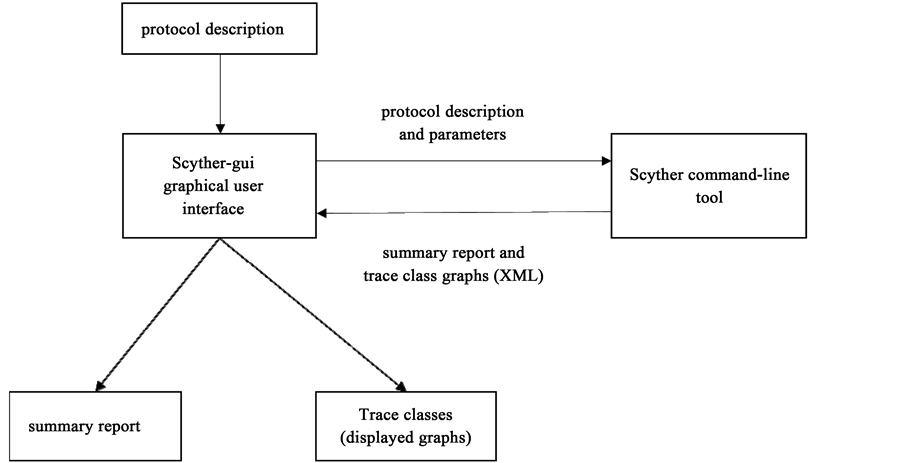
GitHub - binhnguyen1984/scyther-abstraction: The Scyther-abstraction Tool for the symbolic analysis of security protocols

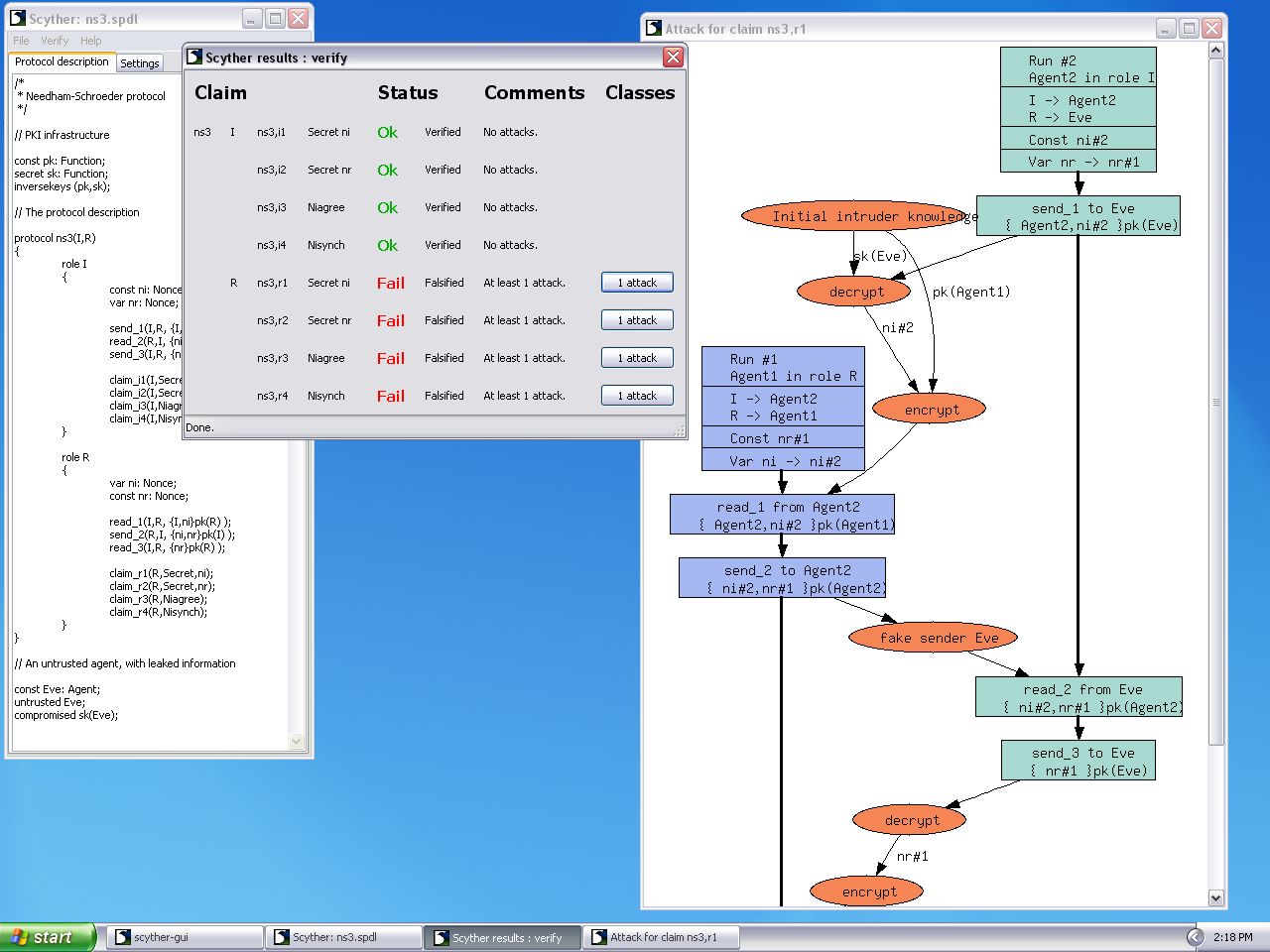
Security verification results of the Khemissa et al.'s protocol using... | Download Scientific Diagram
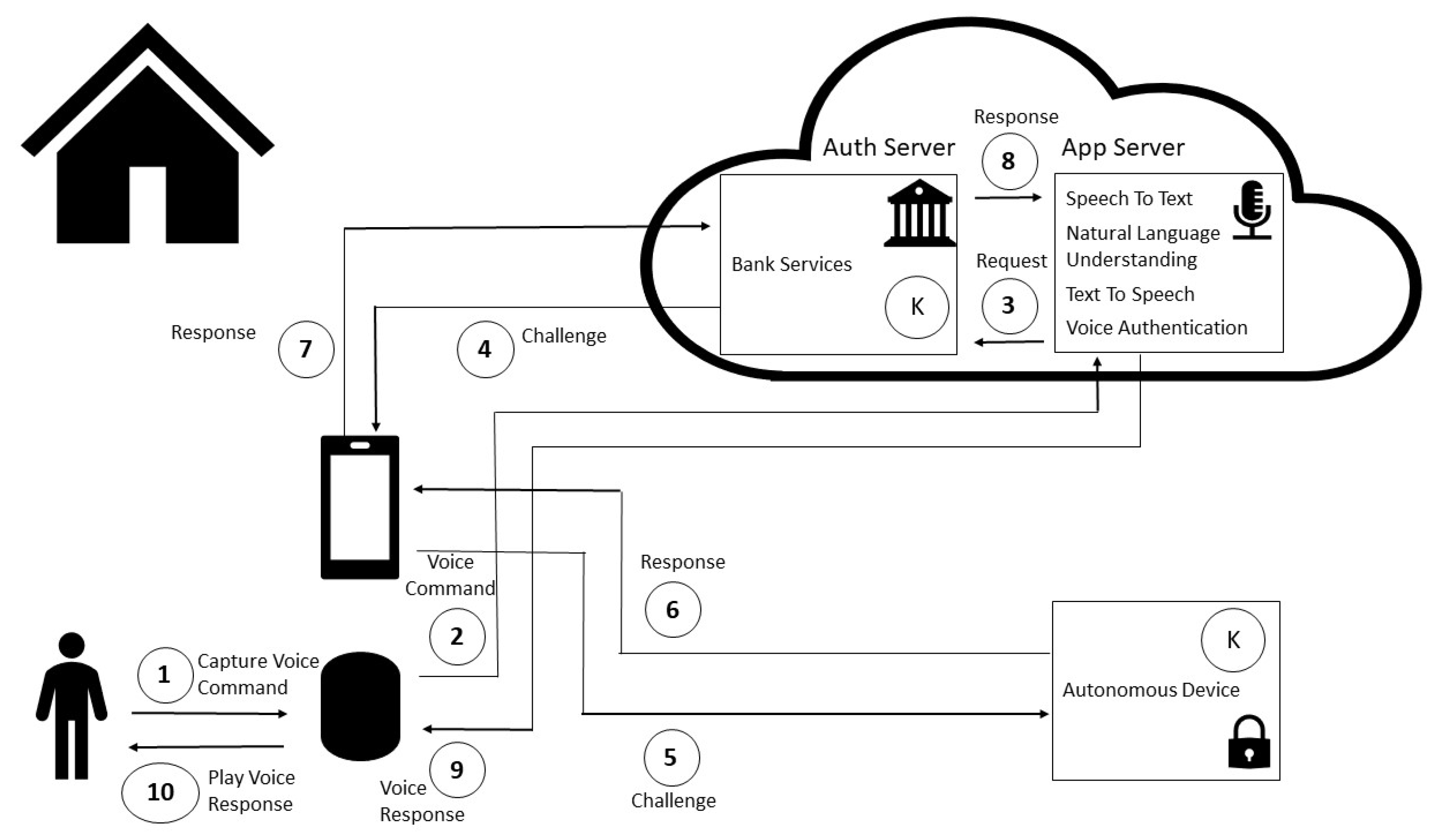
Sensors | Free Full-Text | Non-Invasive Challenge Response Authentication for Voice Transactions with Smart Home Behavior | HTML

Security verification results of the Khemissa et al.'s protocol using... | Download Scientific Diagram