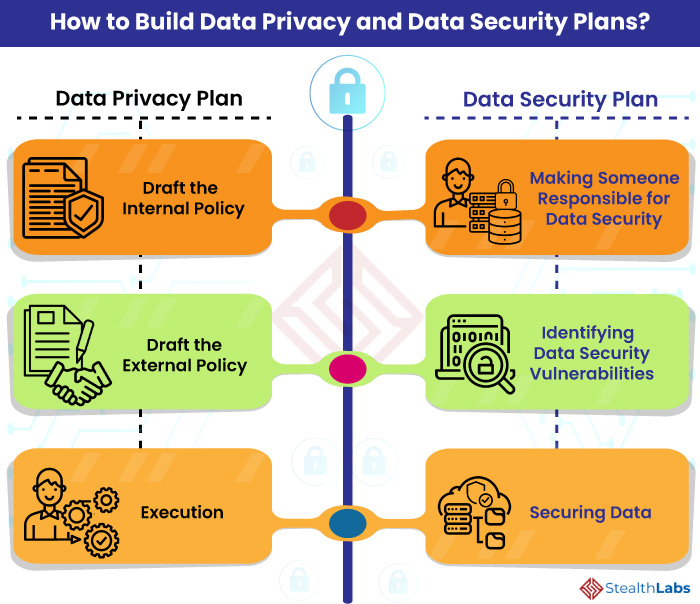
PECB - Key Data Privacy Roles Explained: Data Protection Officer, Information Security Manager, and Information Security Auditor

Data protection, Cyber security, information privacy. Internet and technology concept. Server room background Stock Photo - Alamy
Data Protection Vs Information Security Ppt Inspiration Professional Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Cyber Security, Protection of Information Data. the Concept of Data Protection. Stock Illustration - Illustration of isolated, network: 116535543

Cyber security, data protection,information privacy.Internet and technology concept. Data center, server room Stock Photo - Alamy

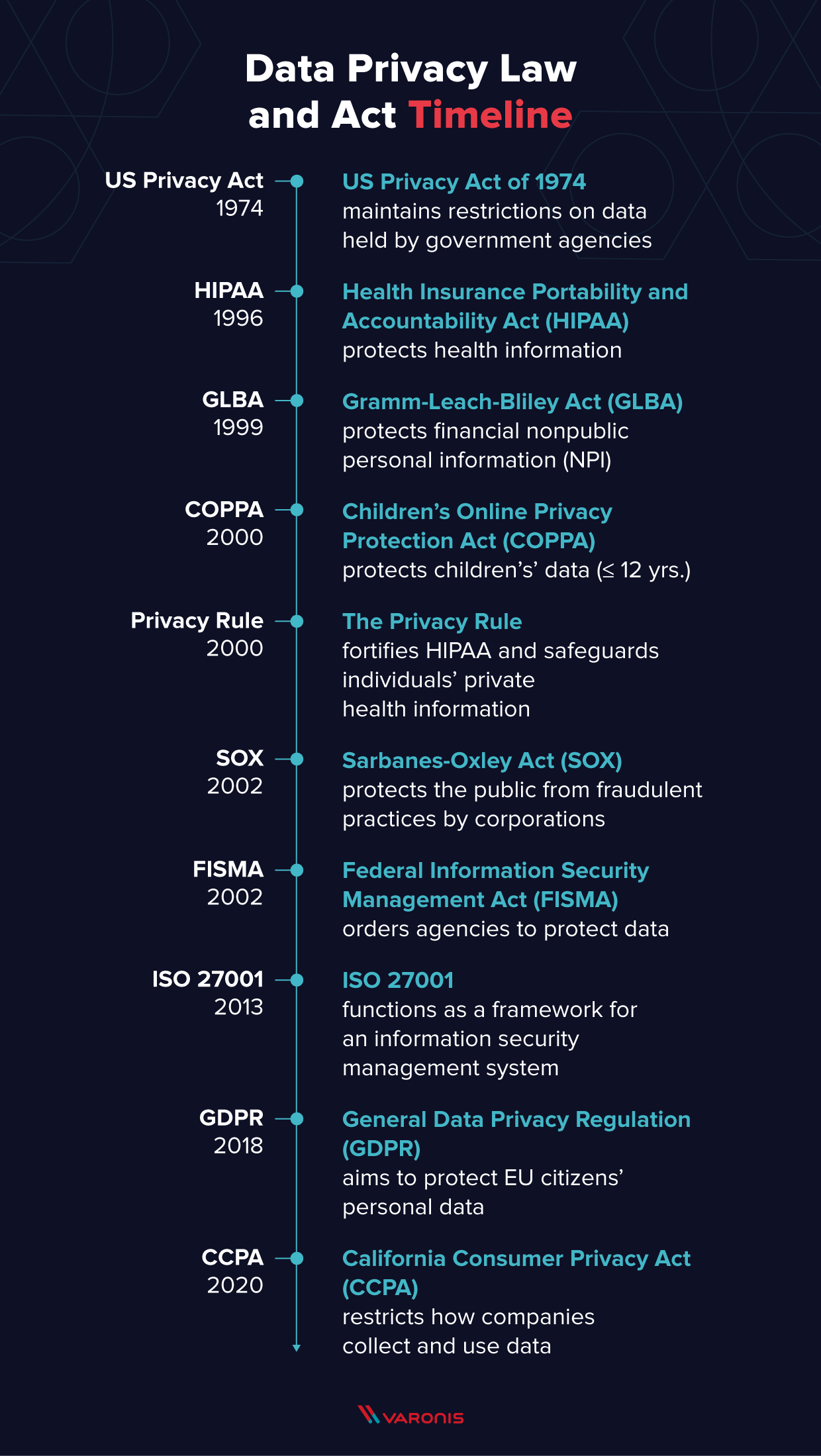


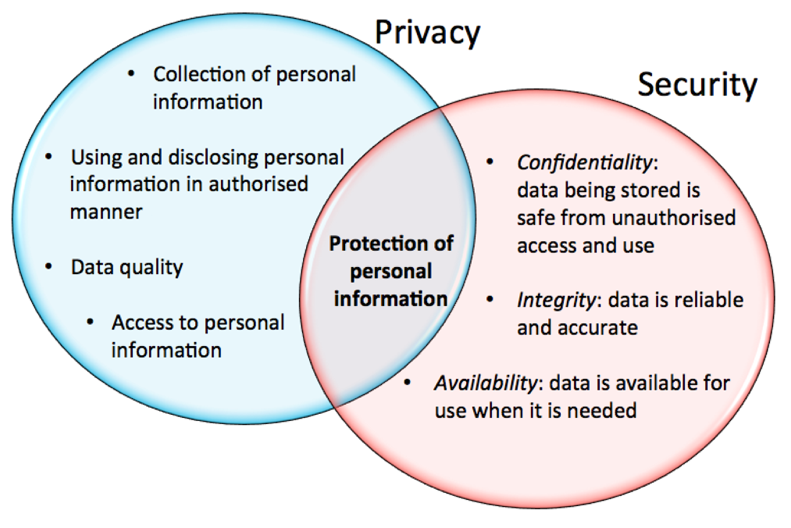
![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2019/10/Data-Privacy-vs.-Data-Security.png)
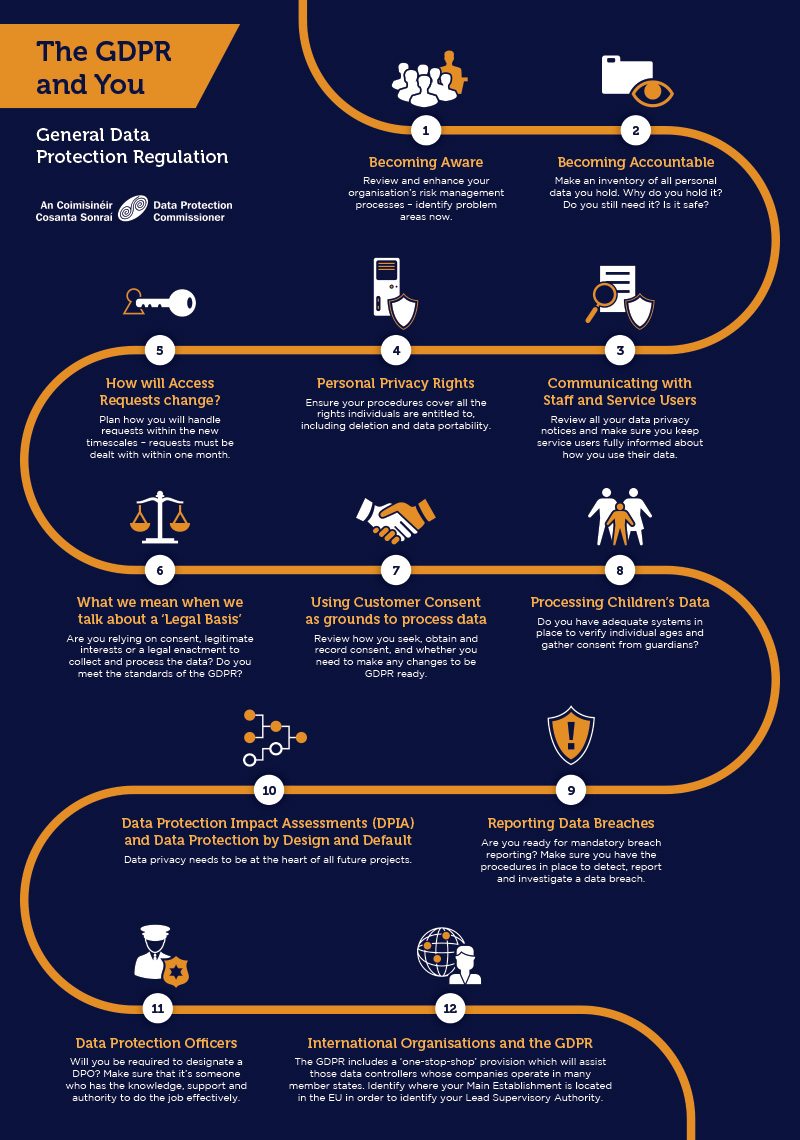

![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2020/08/visual-representation-of-data-privacy-and-data-security-areas.png)