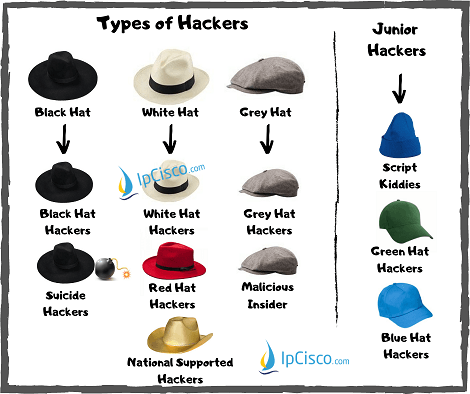
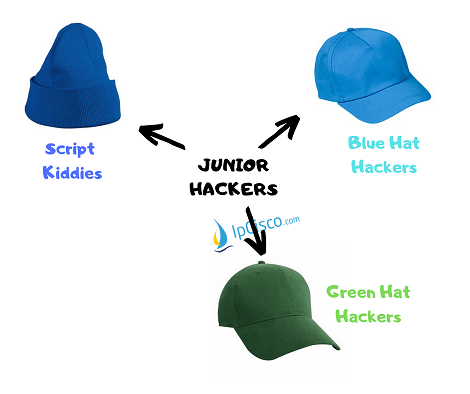
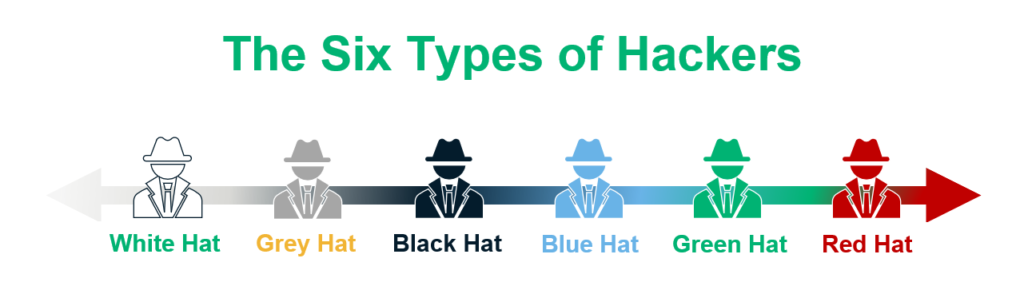
Hacker Black Hat Briefings, PNG, 1600x1600px, Hacker, Area, Black Hat Briefings, Blue, Headgear Download Free

Writing Note Showing Blue Hat Hacker. Business Photo Showcasing Person Consulting Firms Who Bug System Prior To Its Stock Photo - Image of control, attack: 138946654

Word Writing Text Blue Hat Hacker. Business Concept for Person Consulting Firms Who Bug System Prior To Its Launch Color Stock Illustration - Illustration of demonstratingal, cyber: 138958225